I work on information security promotion
Information security basic policy
As jig, C/F production company in us about car "better prices, better efficiency with a better product" in a motto
I performed business as the theme that was the most important by the offer of the product which a customer was satisfied with.
Including the information assets which took from a customer for achievement of this corporate philosophy the information assets of the company from every threat
Including the information assets which took from a customer for achievement of this corporate philosophy the information assets of the company from every threat
It recognizes it to be our important management problem to secure enough information security measures to protect it,
I set a policy as follows and promote this.
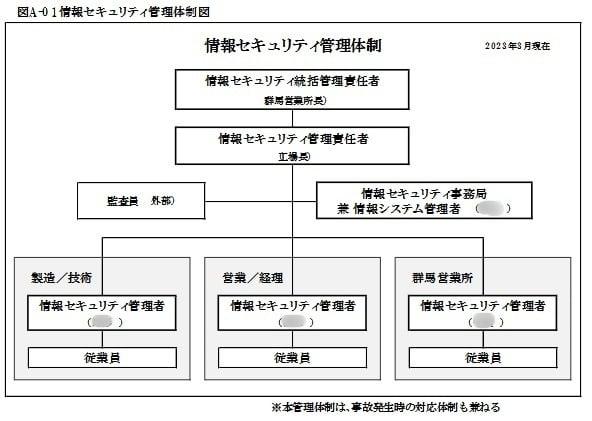
(1) Information security regime
I establish an organization to manage the information security transversely, and to promote all companies.
(1) Information security regime
I establish an organization to manage the information security transversely, and to promote all companies.
(2) Enforcement of the risk assessment
We investigate a threat, weakness from the viewpoint of secrecy, integrity, availability about information assets to hold,
We investigate a threat, weakness from the viewpoint of secrecy, integrity, availability about information assets to hold,
I grasp an inherent risk.
In addition, I carry out risk assessment depending on a periodical and serious change again.
In addition, I carry out risk assessment depending on a periodical and serious change again.
(3) Enforcement of information security measures
We make necessary information security measures clear as a result of risk assessment,
I carry out measures activity faithfully.
(4) Enforcement of the education for improvement in information security
We carry out education regularly and as needed, a basic policy in the information security and
About the importance of satisfying a purpose, responsibility under the law, all employees can continue having recognition
I will execute a program.
(5) Enforcement of the review by self-check and the inspection
We carry out self-check and inspection about the management situation of the information security regularly and as needed,
I will carry out a review of a regime and the structure.
(6) Continuous improvement
We grasp the situation inside and outside the organization about the information security, continuous improvement for the information security
I work on this.
(7) Legal compliance
We laws and ordinances, guidelines in conjunction with the information security and the duty in the contract and official regulations in the company
I will observe it.
March, 2023
Fuji Seimitsu Kougyou Co., Ltd.
President Yasutaka Tanaka
Fuji Seimitsu Kougyou Co., Ltd.
President Yasutaka Tanaka
Information security basics rule
・A confidential information and secret type
・Daily life management ① basics ② surroundings of the confidential information
・Entrance management of a factory, the office
・I take the security ① data sharing ② password ③ outside recording medium of the PC
・The use of the E-mail
・The use of smartphone, SNS(SMS)
・The preparation to a cyber attack
・The example which is targeted for incident handle ① basic ② report
・Daily life management ① basics ② surroundings of the confidential information
・Entrance management of a factory, the office
・I take the security ① data sharing ② password ③ outside recording medium of the PC
・The use of the E-mail
・The use of smartphone, SNS(SMS)
・The preparation to a cyber attack
・The example which is targeted for incident handle ① basic ② report
Information security activity report
2023-06-21
2022-12-05